An IAM (Identity and Access Management) permission boundary is an advanced feature in AWS that defines the maximum permissions an IAM entity such as a user, group, or role can have. It acts as a restrictive barrier that limits the permissions that can be attached to an IAM entity, ensuring that even if more expansive permissions are granted directly or through group memberships, the entity’s effective permissions are capped by the permission boundary.
This is particularly useful in scenarios where you want to delegate certain administrative tasks to users or roles without granting them unfettered access. By setting a permission boundary, you can enforce a stricter access control that mitigates the risk of unintended access to sensitive actions.
It’s important to note that a permission boundary in itself does not grant permissions, but rather restricts the maximum permissions that an IAM entity can assume. It works in conjunction with IAM policies, which explicitly grant permissions to those IAM entities.
In essence, the permissions actually granted to an IAM entity is the permission contained within the overlapping intersections of the policy attached to the entity and the IAM boundary itself (in addition to any restrictions presented by an SCP).
In essence, the permissions actually granted to an IAM entity is the permission contained within the overlapping intersections of the policy attached to the entity and the IAM boundary itself (in addition to any restrictions presented by an SCP).

Example:
Bob is a user that is assigned the System Administrator which is comprised of the following Permissions: EC2:* ; Lambda:* ; and ECS:*. Attached to Bob’s role is a Permission boundary stating that the maximum permissions Bob’s role can have is EC2:* ; Lambda:* ; and CloudWatch:*.
Although Bob’s role itself shows that he has the ability to use ECS:*, because this permission does not fall within the intersection of the two policies, Bob will get a permission denied error from AWS specifying that the policy is not found in the Permission Boundary.
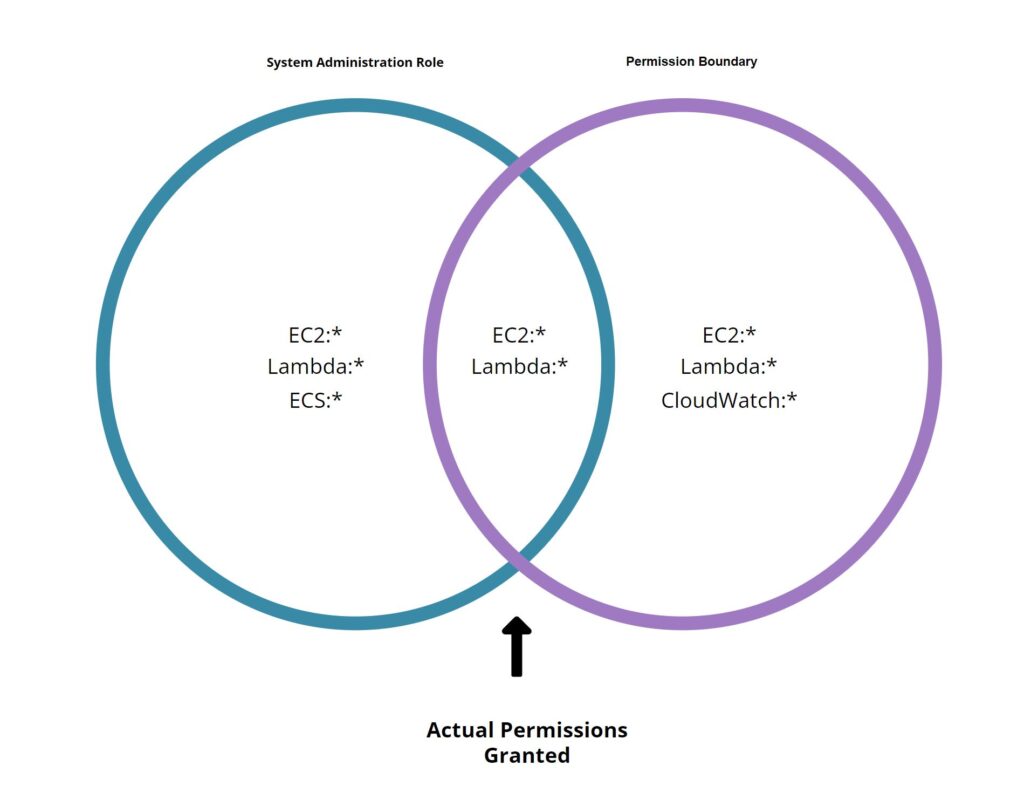
Additionally, if Bob attempts to perform any actions within CloudWatch, he will be unable to perform that action because this permission has not been assigned to his role.
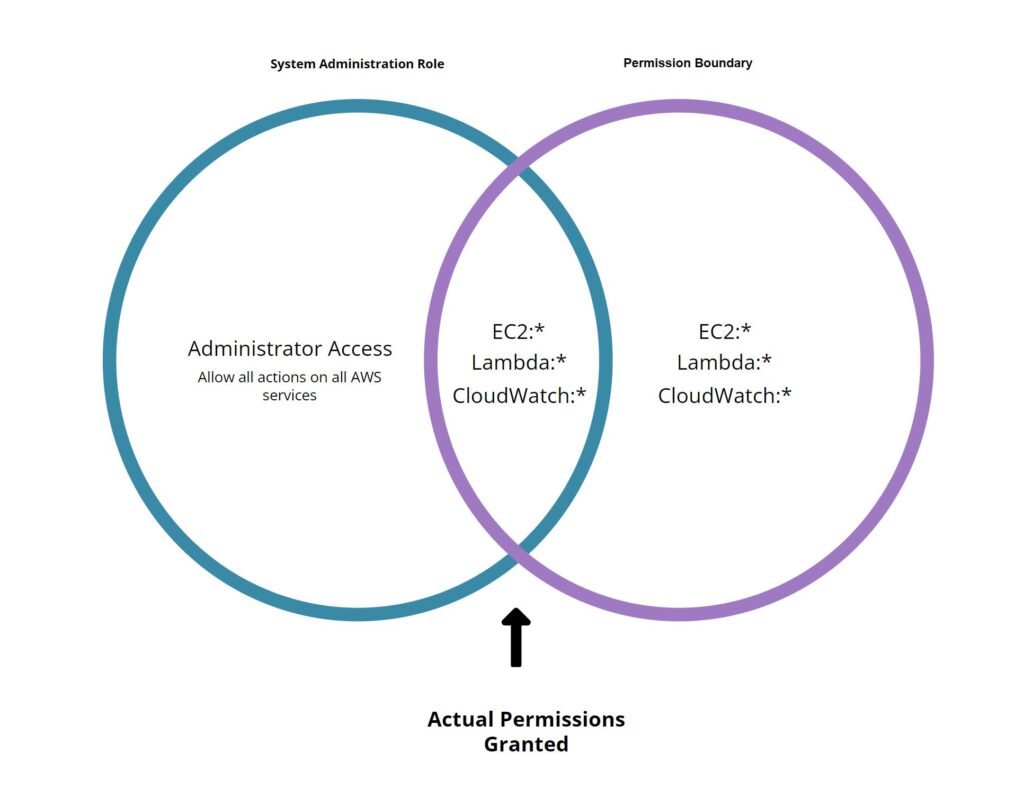
Even if an administrator were to attach the AWS Administrator access policy to Bob’s role, Bob would still only be allowed to perform the actions outlined in the intersection of the two policies, otherwise AWS would again respond with a permission denied error.
See the AWS Docs for more information.
